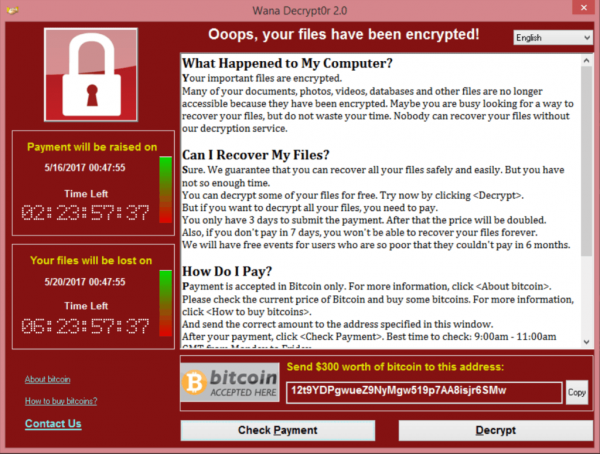
Ooops, your files have been encrypted!
They have Illustrious names like WannaCry, LockerGoga, Bad Rabbit and NotPetya and are insidious. Once they have established themselves in the corporate network, things get tricky. Ransomware has become a lucrative business model for cyber criminals and the stream of new variants is not stopping. On the contrary. We must all prepare for an expansion of this malware. A situation report.
The last semi-annual report of Reporting and Analysis Centre for Information Assurance MELANI of the Swiss Federal Administration reads like a detective story. Ransomware occupies a considerable part of the plot as a “focal topic”. This is especially due to the fact that encryption trojans are no longer comparable with earlier versions in terms of diversity and damage potential. Today, Ransomware can paralyze companies in one fell swoop and threaten their existence. There are plenty of examples.
Sneaky methods
The criminals who use Ransomware try to enrich themselves by extorting a ransom from a company in the form of Bitcoins or similar crypto tokens. The victims are potentially blackmailable because they have been infiltrated with malware that encrypts files on the computer and connected network drives and thus makes them unusable – or copies files to blackmailers. Attackers usually use trusted emails with malicious attachments or fatal download links. The affected user is then confronted with a lock screen and the payment request mentioned above. Of course there is no guarantee that the files will be decrypted (or not published) after payment and that no further attacks will follow. The mess takes its course, because most companies have neither a defined procedure nor the appropriate tools to proceed purposefully in the event of an infestation.
The typical sequence after an attack
1. Recognition: by chance (user calls Helpdesk)
2. First reaction: panic and random action
3. Source of infection: difficult to locate
4. Ensure that all sources have been cleaned: unsafe
5. Recovery: cumbersome and time-consuming
6. Duration to stabilization of the system: days to weeks
Take precautions
Hoping that you will not become a victim yourself is a bad strategy. The combination of the following precautions minimizes the risk:
- Sharpen consciousness: Make sure that the users in your company are aware of blackmail Trojans and behave correctly with suspicious e-mails or other sources (e.g. USB stick).
- Anti-malware and extensions: Scan incoming data for malware at the entrance gate. Make sure that antivirus software is used consistently on the clients. Check with your IT partner to see if special anti-ransomware extensions (especially for file services) are available for your environment.
- Updates: All operating systems and client applications must be kept up-to-date.
- Create regular backups: The more backup copies there are, the easier it is for you to recover the intact data after a successful Ransomware attack. Offline backups or media breaks offer additional security.
- Stand by for emergency plan: Make sure your IT crew or IT partner has a tested step-by-step guide in place in the event that a Trojan horse takes effect.
Bottom line
It can affect us all and despite precautions there is no 100 percent protection against Ransomware. But it is possible, with the right measures, to significantly reduce the danger. An end of the attacks is not foreseeable, too lucrative is the Ransomware business model. But those who prepare themselves accordingly have a good chance that the cybercriminal locusts will move on.
Your company’s security is our top priority, and ITpoint is here to support you in developing the necessary security mechanisms to keep your business safe. Our Ransomware Protection Service for NetApp is designed to protect your IT system. With additional security software, you will be able to detect any suspicious access to your file systems early on and take proactive measures to block malware. What’s more, our intelligent system can distinguish between desired access and undesired access, allowing you to take appropriate action.
Blackmail Trojans have become a threat to businesses, but a billion-dollar business for cybercriminals. Patrick Hertig (Chief Security by ITpoint) on how to deal with it.
Does the use of cloud services make companies more vulnerable to Ransomware?
I’m assuming the opposite. This is because cloud service providers take more effective security precautions, sensitize their customers more actively, patch and secure their systems more consistently than most IT departments do. If your question is about cybercriminals getting ransom more conveniently because a cloud infrastructure is used by many businesses: keep in mind that encryption trojans are typically infiltrated through a company’s people. If one company’s files are infected on a cloud infrastructure, this will not affect the other companies on the same physical environment, provided the appropriate security mechanisms are in place.

Which companies in particular must expect to become the target of a ransomware attack?
Blackmail trojans seem to be spreading across all industries and company sizes. The attackers have it easier than ever. Without programming the malware themselves, they can use pre-configured Ransomware-as-a-Service attacks from the Darknet and then collect most of the extorted ransom money for themselves. Ransomware has become a business and unfortunately we all have to learn to live with it. Criminals, however, are usually opportunistic: if the effort becomes too great and there is no short-term success, the target is not worthwhile and they move on. So the most popular targets – as banal as it sounds – are poorly prepared companies.
As a cloud provider, how does ITpoint protect itself and its customers from Ransomware?
We sensitize our employees and customers. Our people know what to do when a customer or we ourselves are affected. We use anti-malware at the gateway and on the clients. All systems are state-of-the-art and are continuously updated. To enable granular recovery, we back up files several times a day. As an extended measure, we implemented additional protection at the storage system level a few months ago and immediately defined a service for our customers. We call it the Ransomware Protection Service. Thanks to a special interface of our NetApp storage systems, on which the files of our customers are stored, we were able to dock a technology from the Swiss software company Cleondris, which makes us very confident.
Why this additional storage-based technology?
It allows us to detect suspicious access early and proactively block malicious changes. The system is based on stopping a user when he starts corrupting data on the file shares. This is exactly what happens after the activation of Ransomware. It also supports us with analysis and restore functionality. This solution, in combination with classic anti-malware software, massively reduces our risk.
Wouldn’t it be better than those affected to simply pay the extortionists the ransom they demanded?
We wouldn’t recommend that. There is no certainty that the data will be decrypted after the payment of the ransom – or that no further attacks will follow. And those who pay ransom finance and encourage the criminals, which leads to the extortion of further victims. Not protecting yourself is not an option. But of course I understand companies that pay a ransom after an attack if the value of the lost data is much higher than the claim or even the company’s existence is in danger.
Your company’s security is our top priority, and ITpoint is here to support you in developing the necessary security mechanisms to keep your business safe. Our Ransomware Protection Service for NetApp is designed to protect your IT system. With additional security software, you will be able to detect any suspicious access to your file systems early on and take proactive measures to block malware. What’s more, our intelligent system can distinguish between desired access and undesired access, allowing you to take appropriate action.